Unlock Remote Access: Secure IoT Device Solutions & Setups
Is it truly possible to control your devices from anywhere in the world, securely and efficiently? The answer, in today's digital landscape, is a resounding yes. Remote IoT router access is not only achievable but increasingly essential for both personal and professional applications.
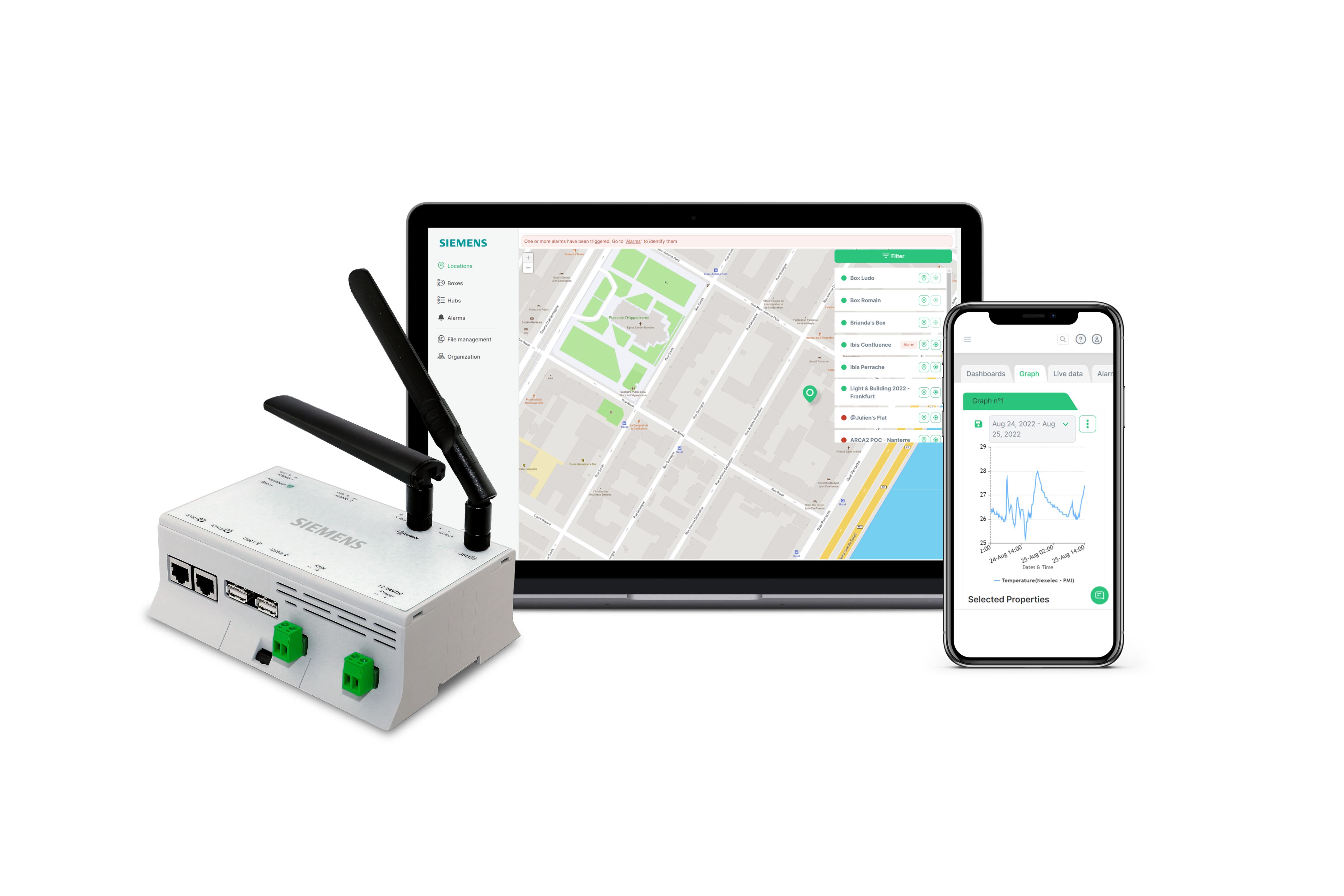
In an era defined by interconnectedness, the capacity to remotely manage Internet of Things (IoT) devices has evolved from a technological novelty to an operational necessity. This holds true for everyone, from the enthusiastic tech hobbyist setting up a smart home, to the small business owner seeking to optimize operational efficiency, and the enterprise IT professional responsible for maintaining complex network infrastructure. Understanding the intricacies of the best remote IoT routers available is the first step towards harnessing the full potential of this technology.
Consider the possibilities: managing smart home devices, such as lighting, climate control, and security systems, from the palm of your hand, regardless of your location. Imagine monitoring critical industrial equipment, diagnosing issues, and implementing solutions without the need for physical presence. This level of control translates to increased efficiency, reduced operational costs, and enhanced security.
The concept of "remote IoT" often brings to mind complex technical configurations. However, with the right tools, a bit of knowledge, and perhaps a cup of coffee, accessing a remote IoT router is not as daunting as it might initially appear. The aim of this exploration is to demystify the process and provide a comprehensive understanding of the best remote IoT setups, particularly those utilizing Raspberry Pi.
These advanced features, combined with robust security protocols, make these routers the backbone of smart device connectivity. They enable seamless communication between devices and networks, ensuring a reliable and secure foundation for your connected ecosystem.
Buying Tips and Best Practices:
Choosing the right IoT/M2M router is a pivotal decision that directly impacts performance and security. The market is saturated with options, each boasting a unique set of features and capabilities. Therefore, a well-informed approach is necessary to ensure that the selected router aligns with your specific needs and project requirements. This guide provides the knowledge and confidence to navigate the complexities of the IoT router landscape.
This isn't just about convenience; it's about unlocking possibilities for smart living, robust security, and unparalleled convenience. This guide is designed to help you establish secure connections, monitor device status, and optimize your IoT infrastructure for peak performance.
Here's a look at the features that make the best remote IoT routers stand out:
- Security Features: Advanced encryption protocols (like OpenVPN, WireGuard), firewalls, and access control lists (ACLs) are crucial to protect your devices and data from unauthorized access.
- QoS (Quality of Service): Prioritize critical traffic to ensure that essential data (like security feeds or critical machine data) always gets through.
- Remote Management: Look for routers with intuitive web interfaces, cloud-based management, and the ability to remotely update firmware.
- Connectivity Options: Consider the different connectivity options supported by the router. This may include Ethernet, Wi-Fi, cellular (4G/5G), and serial interfaces.
- Ease of Use: Whether you're a seasoned techie or new to networking, easy setup and management are essential.
- Cost-Effectiveness: While enterprise-grade routers can be expensive, excellent options exist for small businesses and home use at more reasonable prices.
Remote SSH Access Behind Firewalls
Setting up remote SSH access to your IoT devices behind a firewall or NAT router is a common and often necessary task. The process, while seemingly complex, is entirely manageable. The essence of this setup is to create a secure tunnel through which you can access your device remotely. Here's a breakdown of the key steps and considerations:
- Port Forwarding: The most critical step is configuring port forwarding on your router. This allows incoming traffic on a specific port (typically port 22 for SSH) to be directed to the internal IP address of your IoT device.
- Static IP Address: Assign a static IP address to your IoT device. This ensures that the IP address doesn't change, which would break the port forwarding configuration.
- Dynamic DNS (Optional): If your public IP address is dynamic (changes periodically), use a Dynamic DNS (DDNS) service to map a domain name to your changing IP address.
- Firewall Configuration: Ensure that your router's firewall allows incoming SSH connections on the forwarded port.
- SSH Client: Use an SSH client (like PuTTY on Windows or the built-in SSH client on Linux/macOS) to connect to your device using your public IP address or DDNS hostname and the port number.
Monitoring IoT Device Status
A crucial aspect of remote IoT management is the ability to monitor the status and health of your devices. This includes critical metrics such as device uptime, CPU usage, memory consumption, network activity, and SD card health.
- System Monitoring Tools: Leverage system monitoring tools like `top`, `htop`, and `iotop` on your device to get real-time insights into resource utilization.
- SD Card Health Monitoring: Regularly check the SD card's health to prevent data corruption. Use tools like `smartmontools` (if supported) or specialized SD card health utilities.
- Remote Logging: Implement a remote logging system to collect log data from your device and centralize it for analysis.
- Alerting: Configure alerts to be notified of critical events, such as device outages, low disk space, or high CPU usage.
Securing Remote Access Over the Internet
Securing remote access over the internet is paramount. Implement the following measures to protect your IoT devices:
- Strong Passwords: Always use strong, unique passwords for all your devices and user accounts.
- Two-Factor Authentication (2FA): Enable 2FA wherever possible to add an extra layer of security.
- Firewall Rules: Configure robust firewall rules on your router and device to restrict incoming traffic.
- VPN: Using a VPN is a great idea.
- Regular Updates: Keep your device's operating system and software updated to patch security vulnerabilities.
- Limit Exposure: Minimize the number of open ports and services.
Remote IoT API & Integration
APIs and integration capabilities are key to creating advanced remote IoT solutions. A well-designed API enables greater automation and integration of remote IoT services into your system. APIs facilitate:
- Data Collection & Analysis: APIs streamline the process of collecting data from your devices and integrating it into analytics platforms.
- Automation: You can automate device management tasks such as reboots, firmware updates, and configuration changes.
- Integration with Other Systems: APIs allow you to seamlessly integrate your IoT devices with other systems.
- Remote Control & Configuration: APIs provide a programmatic interface to control and configure your devices remotely.
RemoteIoT Solutions and Optimization
The best remote IoT solutions are not one-size-fits-all. The optimal solution is dictated by your specific needs, technical expertise, and budget. Here's a look at some leading options and their benefits:
- Raspberry Pi with OpenVPN: A cost-effective and versatile solution for creating a secure VPN server on your home network.
- Commercial VPN Routers: These routers are designed to provide ease of use and robust security features.
- Cloud-Based IoT Platforms: Offer comprehensive management and monitoring capabilities.
Setting up a Raspberry Pi
Raspberry Pi's versatility, low cost, and open-source nature make it a fantastic solution for many remote IoT setups. Here's a breakdown of how to use Raspberry Pi with a VPN:
- Choose Your Hardware: Select a Raspberry Pi model that meets your performance requirements (Raspberry Pi 3 or 4 are recommended).
- Install the Operating System: Flash the Raspberry Pi OS (formerly Raspbian) onto an SD card.
- Enable SSH: Enable SSH access during the initial setup of your Raspberry Pi.
- Configure the VPN: Install and configure a VPN software (OpenVPN is a popular choice).
- Configure Port Forwarding: Set up port forwarding on your router to forward traffic to your Raspberry Pi.
- Test Your Connection: Test your setup.
Remote access behind a router isn't just about convenience; it's about efficiency and security. It is no longer a daunting task and is straightforward with the right knowledge. By mastering the fundamentals of remote IoT router access, you'll be well-equipped to build a secure, efficient, and intelligent network that supports all of your connected devices.
Choosing the Right Remote IoT Router
The choice of a remote IoT router should be a deliberate process. The correct router will act as the reliable foundation for all the devices connected to the network and will enable effortless and secure communication between the IoT devices and other networks. There are a few important factors to consider.
- Connectivity: Decide how the router will connect to the internet. Options include Ethernet, Wi-Fi, and cellular (4G/5G) to cater to different environments.
- Security Protocols: Ensure that the router has a good selection of security features.
- User Interface: Select a router with an easy-to-use interface for configuration and management. A user-friendly interface will make setup and maintenance significantly easier.
- Price: Evaluate the features and functionality of different routers.
The benefits of managing your devices remotely are clear.
The ability to securely access and control IoT devices remotely has become a critical capability for businesses and individuals alike. This remote access is no longer just about convenience; it is about efficiency and security, making it essential for those managing IoT devices. To be effective you need the right tools, technical knowledge, and careful planning.